Week 1 | Week 2 | Week 3 | Week 4 | Week 5 | Week 6 | Week 7 | Week 8 | Week 9 | Week 10
Why the Data Lifecycle Matters
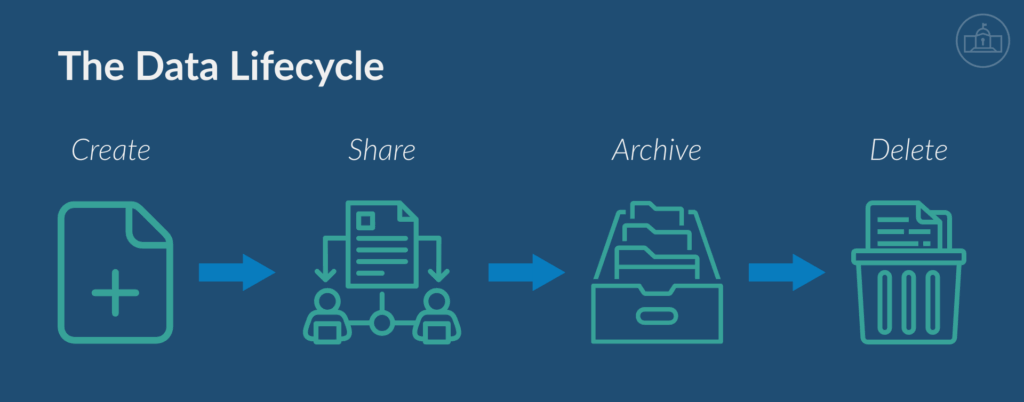
In public-sector environments, data is constantly in motion—created, shared, stored, and often retained longer than necessary. As it moves across systems and users, the risk grows—especially when organizations lose track of where data lives or who can access it.
Managing the data lifecycle is essential to protecting public systems, ensuring confidentiality, and upholding trust.
How Risk Accumulates Across the Lifecycle
Most files don’t stay in one place.
They’re:
- Emailed to teammates Saved in multiple cloud locations
- Backed up to systems that aren’t regularly monitored
- Left in inboxes, folders, or shared drives well past their relevance
Each of these stages increases your attack surface— not because the data is inherently dangerous, but because it may no longer be protected.
Risk increases when:
- Files are no longer monitored
- Permissions outlive their purpose
- System ownership changes but legacy data remains
The result? Exposure points that are difficult to detect but easy to exploit.
Beyond Compliance: Lifecycle Management in the Cloud
GovRAMP supports public sector cybersecurity by setting clear expectations for how data should be handled—not just when it’s active, but throughout its entire lifecycle.
That includes:
- Who has access to sensitive information
- How and where data is stored or encrypted
- What happens to data when systems are retired or contracts expire
Through baseline security controls, continuous monitoring requirements, and third-party assessments, GovRAMP helps ensure cloud service providers are equipped to protect data from start to finish.
Lifecycle awareness is a core expectation across all GovRAMP security statuses.
Practical Questions To Ask
Good data lifecycle management starts with visibility and intentionality. Teams can begin by asking:
- What types of data are we collecting?
- Where is that data stored?
- Who currently has access—and who no longer needs it?
- When is the right time to archive, transfer, or delete information?
These aren’t one-time questions—they’re part of an ongoing posture of risk reduction, access control, and shared responsibility.
GovRAMP’s Role in Securing the Lifecycle
The risk isn’t just about what data you have—it’s about what you forget you have.
GovRAMP helps ensure government organizations don’t inherit unnecessary vulnerabilities through forgotten storage locations, orphaned files, or overshared assets.
We do this by:
- Working with cloud providers to verify secure storage, retention, and deletion processes
- Supporting public agencies in selecting solutions that meet rigorous standards
- Aligning best practices across industry and government through a shared framework
The result is a more complete view of risk—one that includes everything from provisioning to decommissioning.
Takeaway: Respect the Full Lifecycle
Managing cybersecurity risk requires more than protecting what’s in front of you. It means protecting what’s behind you, too.
Data that’s no longer needed should be handled with as much care as data in active use. Because in the end, the longer data goes unmanaged, the more risk it carries.
Good cybersecurity starts with knowing where your data goes—and making sure it doesn’t stay longer than it should.

