-
Government
-
Service Providers
-
Assessors
-
Resources
-
About

In cybersecurity, especially in the public sector, clarity matters. Terms like “threat” and “vulnerability” are often used interchangeably, but they are not the same. And understanding the difference isn’t just a technical detail—it’s essential to managing risk, securing systems, and protecting the people who rely on public services every day.
This distinction is foundational to GovRAMP’s mission. We work to ensure government agencies have access to secure cloud technologies, and that providers understand what it takes to meet those expectations. Recognizing the difference between threats and vulnerabilities is step one in that process.
Imagine a thunderstorm.
Now imagine a house.
The storm rolling in? That’s a threat.
A window left open? That’s a vulnerability.
The rain that pours in and causes damage?
That’s risk realized.
It’s a simple analogy, but one that reflects the reality behind many cybersecurity incidents: an external danger meets an internal weakness—and the consequences follow.
A threat is any external force that can cause harm to your systems, data, or operations.
Threats may be intentional—such as a cyberattack—or accidental, such as a natural disaster or human error. What they have in common is that they originate outside your organization, and they often exist regardless of your level of preparation.Examples include:
Threats can’t always be predicted, and they can’t be eliminated—but they can be accounted for.
A vulnerability is a weakness in your system, process, or people that allows a threat to succeed.
Unlike threats, vulnerabilities are internal—and they’re often within your control to identify and fix. They may stem from outdated technology, misconfigurations, or gaps in training or procedures.
Examples include:
On their own, vulnerabilities don’t cause harm. But they open the door for threats to do so.
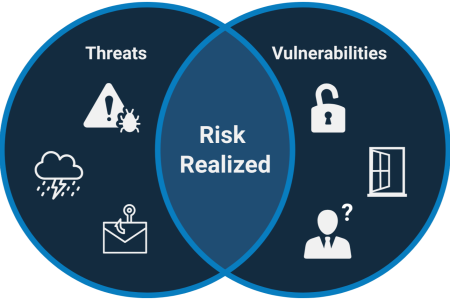
Risk happens when a threat meets a vulnerability.
Here’s how that plays out in practice:
A phishing email (threat) lands in a user’s inbox.
The user clicks the link (vulnerability).
Credentials are stolen, and systems are compromised. → Risk realized
A malicious actor scans for exposed systems (threat).
A legacy database is still online and unprotected (vulnerability).
Sensitive data is extracted. → Risk realized
When public-sector organizations understand both sides of this equation, they’re better equipped to prevent disruption and build more secure systems.
GovRAMP exists to protect the public sector from adopting software and services that introduce unnecessary risk.
We set and manage a standardized framework that enables government organizations to procure secure cloud solutions—and gives providers a clear path to demonstrate they meet those standards. Our Program Management Office (PMO) helps private sector vendors identify and address vulnerabilities as they work toward verified status.
In doing so, we’re not just safeguarding agency systems. We’re helping agencies maintain the integrity of the services that citizens rely on: from digital classrooms to public utilities, healthcare systems to local permitting portals.
Secure procurement protects systems. But more importantly, it protects people.
Every organization has vulnerabilities. Acknowledging them isn’t a weakness—it’s the first step toward building resilience.
You may not be able to prevent every threat.
But you can:
Whether you’re responsible for implementing secure technology or evaluating vendor submissions, understanding threats and vulnerabilities will guide smarter decisions—and help reduce risk before harm occurs.
So ask yourself:
Where are our open windows?
And how can we close them—before the storm arrives?